“DevSecOps: Seamlessly Embedding Security into Every Line of Code.”
Introduction
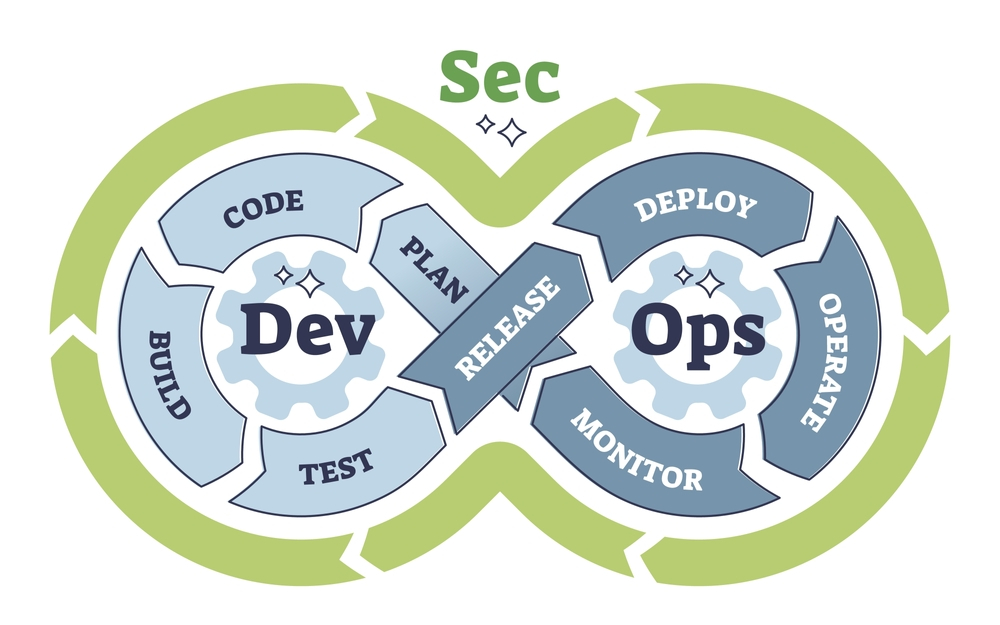
DevSecOps is an evolution of the DevOps methodology that emphasizes the integration of security practices within the DevOps pipeline. As organizations increasingly adopt agile development and continuous delivery practices, the need for robust security measures becomes paramount. DevSecOps aims to embed security at every stage of the software development lifecycle, from planning and coding to testing and deployment. By fostering a culture of collaboration between development, operations, and security teams, DevSecOps ensures that security is a shared responsibility rather than an afterthought. This proactive approach not only enhances the security posture of applications but also accelerates the delivery of secure software, ultimately enabling organizations to respond swiftly to emerging threats while maintaining compliance with regulatory standards.
Security Automation in DevSecOps Pipelines
In the rapidly evolving landscape of software development, the integration of security into DevOps practices has become paramount. This integration, known as DevSecOps, emphasizes the importance of embedding security measures throughout the software development lifecycle rather than treating them as an afterthought. A critical component of this approach is security automation, which plays a vital role in enhancing the efficiency and effectiveness of security practices within DevSecOps pipelines. By automating security processes, organizations can not only streamline their workflows but also ensure that security is consistently applied across all stages of development.
Security automation in DevSecOps pipelines involves the use of tools and technologies to automatically identify, assess, and mitigate security vulnerabilities. This proactive approach allows teams to detect potential threats early in the development process, thereby reducing the risk of security breaches and minimizing the time and resources required for remediation. For instance, automated security testing tools can be integrated into continuous integration and continuous deployment (CI/CD) pipelines, enabling developers to receive immediate feedback on security issues as they write code. This immediate feedback loop fosters a culture of security awareness among developers, encouraging them to prioritize security considerations from the outset.
Moreover, the implementation of security automation facilitates the consistent application of security policies across various environments. By utilizing automated compliance checks, organizations can ensure that their applications adhere to industry standards and regulatory requirements. This not only helps in maintaining compliance but also reduces the likelihood of human error, which can often lead to security vulnerabilities. As a result, teams can focus on innovation and development, knowing that security measures are being enforced automatically.
In addition to automated testing and compliance checks, security automation encompasses the use of threat intelligence and monitoring tools. These tools can continuously analyze application behavior and network traffic to identify anomalies that may indicate a security threat. By leveraging machine learning and artificial intelligence, organizations can enhance their threat detection capabilities, allowing them to respond to potential incidents more swiftly and effectively. This real-time monitoring is crucial in today’s threat landscape, where cyberattacks are becoming increasingly sophisticated and frequent.
Furthermore, the integration of security automation into DevSecOps pipelines promotes collaboration between development, security, and operations teams. By breaking down silos and fostering a shared responsibility for security, organizations can create a more cohesive approach to risk management. This collaboration is essential for ensuring that security is not viewed as a hindrance to development but rather as an integral part of the process. As teams work together to automate security practices, they can share insights and best practices, ultimately leading to a more secure and resilient software development environment.
In conclusion, security automation is a cornerstone of effective DevSecOps pipelines, enabling organizations to integrate security seamlessly into their development processes. By automating security testing, compliance checks, and threat monitoring, teams can enhance their ability to identify and mitigate vulnerabilities early in the development lifecycle. This proactive approach not only improves security outcomes but also fosters a culture of collaboration and shared responsibility among development, security, and operations teams. As organizations continue to embrace DevSecOps, the role of security automation will undoubtedly become increasingly critical in safeguarding applications and data against evolving cyber threats.
Best Practices for Implementing DevSecOps
Implementing DevSecOps effectively requires a strategic approach that integrates security practices into the DevOps pipeline without disrupting the agile nature of development and operations. One of the best practices for achieving this integration is to foster a culture of shared responsibility among all team members. By promoting the idea that security is not solely the responsibility of a dedicated security team, organizations can encourage developers, operations personnel, and security experts to collaborate closely. This cultural shift not only enhances communication but also ensures that security considerations are embedded in every phase of the software development lifecycle.
Another essential practice is to automate security testing and compliance checks within the CI/CD pipeline. Automation allows for continuous security assessments, enabling teams to identify vulnerabilities early in the development process. By integrating tools that perform static application security testing (SAST), dynamic application security testing (DAST), and software composition analysis (SCA), organizations can ensure that security is continuously monitored. This proactive approach minimizes the risk of vulnerabilities making their way into production, thereby reducing the potential for costly breaches and compliance issues.
In addition to automation, it is crucial to implement security as code. This practice involves defining security policies and controls in a code format, which can be versioned and managed just like application code. By treating security configurations as code, teams can ensure that security policies are consistently applied across environments, making it easier to track changes and maintain compliance. Furthermore, this approach allows for rapid iteration and adaptation of security measures in response to evolving threats, thereby enhancing the overall security posture of the organization.
Moreover, continuous education and training for all team members play a vital role in the successful implementation of DevSecOps. Regular training sessions on secure coding practices, threat modeling, and the latest security trends can empower developers and operations staff to make informed decisions regarding security. By fostering a mindset of security awareness, organizations can cultivate a workforce that is not only skilled in their respective roles but also vigilant about potential security risks.
Collaboration with external security experts can also enhance the effectiveness of DevSecOps practices. Engaging with third-party security consultants or utilizing managed security services can provide organizations with additional insights and expertise that may not be available in-house. This collaboration can help identify blind spots in existing security measures and offer recommendations for improvement, ultimately leading to a more robust security framework.
Furthermore, organizations should prioritize the implementation of a feedback loop within their DevSecOps processes. By continuously gathering feedback from security assessments, incident responses, and team retrospectives, organizations can identify areas for improvement and adapt their practices accordingly. This iterative approach not only enhances security measures but also fosters a culture of continuous improvement, which is essential in today’s rapidly changing threat landscape.
Lastly, it is important to measure and report on security metrics to demonstrate the effectiveness of DevSecOps initiatives. By establishing key performance indicators (KPIs) related to security, such as the number of vulnerabilities detected, time to remediate issues, and compliance status, organizations can gain valuable insights into their security posture. These metrics can also serve as a basis for informed decision-making and resource allocation, ensuring that security remains a priority as development and operations evolve.
In conclusion, implementing DevSecOps requires a multifaceted approach that emphasizes collaboration, automation, education, external expertise, feedback, and measurement. By adopting these best practices, organizations can effectively integrate security into their DevOps pipelines, ultimately leading to more secure software delivery and a stronger overall security posture.
The Role of Continuous Monitoring in DevSecOps
In the rapidly evolving landscape of software development, the integration of security into the DevOps pipeline has become increasingly critical. This integration, known as DevSecOps, emphasizes the importance of embedding security practices throughout the software development lifecycle. A pivotal component of this approach is continuous monitoring, which plays a vital role in ensuring that security measures are not only implemented but also maintained and adapted in real-time. Continuous monitoring involves the ongoing assessment of applications, infrastructure, and processes to identify vulnerabilities, threats, and compliance issues as they arise.
To begin with, continuous monitoring facilitates a proactive security posture. Traditional security measures often rely on periodic assessments, which can leave significant gaps in protection. In contrast, continuous monitoring allows organizations to detect and respond to security incidents as they occur, thereby minimizing potential damage. By employing automated tools and techniques, teams can continuously analyze system behavior, network traffic, and user activities, enabling them to identify anomalies that may indicate a security breach. This real-time visibility is essential for organizations that operate in dynamic environments where threats can emerge unexpectedly.
Moreover, continuous monitoring enhances collaboration among development, security, and operations teams. In a DevSecOps framework, these teams work together to ensure that security is a shared responsibility rather than the sole domain of a separate security team. By integrating continuous monitoring into the DevOps pipeline, all stakeholders can access the same data and insights, fostering a culture of transparency and collaboration. This shared understanding not only improves the overall security posture but also accelerates the development process, as teams can quickly address vulnerabilities without waiting for lengthy security assessments.
In addition to fostering collaboration, continuous monitoring supports compliance with regulatory requirements and industry standards. Many organizations operate in highly regulated environments where adherence to security protocols is mandatory. Continuous monitoring provides the necessary oversight to ensure that security controls are functioning as intended and that any deviations from compliance are promptly addressed. By automating compliance checks and generating real-time reports, organizations can demonstrate their commitment to security and compliance, thereby reducing the risk of penalties and reputational damage.
Furthermore, the insights gained from continuous monitoring can inform future development efforts. By analyzing data on security incidents and vulnerabilities, organizations can identify patterns and trends that may indicate systemic issues within their applications or infrastructure. This information can then be used to refine development practices, implement more robust security controls, and prioritize areas for improvement. In this way, continuous monitoring not only serves as a reactive measure but also as a proactive tool for enhancing the overall security framework.
As organizations increasingly adopt cloud-based services and microservices architectures, the complexity of their environments grows, making continuous monitoring even more essential. The dynamic nature of these systems requires a security approach that can adapt to rapid changes and scale accordingly. Continuous monitoring provides the agility needed to keep pace with these developments, ensuring that security measures remain effective in the face of evolving threats.
In conclusion, continuous monitoring is a cornerstone of the DevSecOps approach, enabling organizations to maintain a robust security posture in an ever-changing landscape. By facilitating real-time visibility, fostering collaboration, ensuring compliance, and informing future development efforts, continuous monitoring empowers teams to integrate security seamlessly into their DevOps pipelines. As the importance of security continues to rise, organizations that prioritize continuous monitoring will be better equipped to navigate the complexities of modern software development while safeguarding their assets and data.
Conclusion
DevSecOps represents a crucial evolution in the software development lifecycle by embedding security practices within DevOps pipelines. This integration ensures that security is a shared responsibility among all team members, fostering a culture of collaboration and proactive risk management. By automating security checks and incorporating security tools throughout the development process, organizations can identify vulnerabilities early, reduce the cost and time associated with fixing security issues, and enhance overall software quality. Ultimately, DevSecOps not only strengthens the security posture of applications but also accelerates delivery, enabling organizations to respond swiftly to market demands while maintaining robust security standards.